|
TECHNOLOGY
Got cyberslackers?
Policies, technology, and monitoring help agencies reduce risks from employee Internet abuse
By John Chivvis
Does your agency take risks? If your employees have access to the Internet, then you may be risking a whole lot more than you think.
“According to a number of studies, more and more employees are using the Internet at work for personal business,” says Craig Fuher, president of iPrevision™, an Internet security solutions provider. “So whether it’s the 50% of employees who receive and circulate inappropriate material using the office network, the 10% who use the network to download illegal music and other media, or the 26% of IT employees who have admitted to distributing confidential information outside the company, you’re seeing a new set of risks that agencies need to protect themselves from.”
That being the case, more and more agencies—including Nulty Insurance in Kalamazoo, Michigan—are turning to Internet usage policies, enforced and backed up by Internet monitoring technology.
“Porn”ucopia of problems
Like many agency principals, Nulty Insurance President Dana Nulty-Beals admits that implementing an Internet usage policy was difficult. “It’s one of those things you wish you didn’t have to do because you want to trust people,” she says. “It goes back to not needing something like this—in this case a usage policy—until you really have a problem.”
The problem for Nulty-Beals was two different employees using the agency Internet connection for downloading pornographic material. Before implementing the policy, she says that it was hard to catch the employees because when she or another employee would stop by their offices, the employees would just “click and close.”
What made it even harder was that one employee would come in on the weekend to use the system, and the other set up his system to automatically purge his browser history to hide his tracks. Ultimately Nulty-Beals and her IT person were able to provide proof of the employees’ activities and eventually terminate their employment.
“It was after the second incident that we started looking at monitoring our employees’ Internet usage,” says Nulty-Beals.
IM, P2P and Webmail threats
The problem with monitoring, though, is that so much of Internet usage goes beyond the basic browser window. It’s the applications that use the Internet to transfer information and communications.
“Instant messaging [IM] is the perfect tool for a cyberslacker,” says Pat Kellner, a business development executive for iPrevision. “That’s because IM can be used to transfer files and information in a way that’s instant and untraceable.” He adds that IM is a “tool of the trade” for a number of identity theft rings for quickly transmitting sensitive data including Social Security numbers, credit card information, and maiden names.
That stuns Nulty-Beals. “We put an Instant Messaging client on our systems for our receptionist as a way for her to let us know we had a call on hold, and we also use it for some intra-office communication,” she says. “While employees can’t access client lists or P&L information, they do have access to customer SSNs and driver’s license numbers. Wow!”
Besides the identity theft risk, IM is also becoming a target of virus-developers and spammers (called SPIM). “Right now, over 40% of the top viruses can propagate through an instant messaging client,” adds Fuher.
Peer-to-peer file transfer programs like LimeWire and Kazaa are another avenue for viruses. “Fortunately for us, nobody downloads any files any more,” says Nulty-Beals. “We’re now all scared to death to do so because the last time someone downloaded a file, it contained a virus and our system was down for two days.”
A greater problem than viruses, though, is the liability issue for being caught illegally downloading music, movie, or game files. Fuher points to an Arizona company with fewer than 50 employees that recently had to pay the recording industry $1 million for copyright violations involving MP3 music that had been stored on the company computer system. “And what’s scary is 77% of companies polled in a 2003 study had detected at least one P2P application on their network,” says Fuher.
A third area of abuse comes from personal e-mail accounts being checked over the Web, such as Hotmail, Yahoo, gMail or AOLMail. “Similar to IM and P2P software, Webmail presents the same confidentiality concerns,” says Kellner. “All protective measures that the business has in place for their corporate e-mail system are compromised when someone uses Webmail, because there’s no record of what was communicated.”
Pandora’s Box meets Panoptech’s box
“For an agency, you have to look for some type of solution that will allow you to monitor and manage those Internet applications—IM, P2P and Webmail—as well as what your employees should or shouldn’t be browsing,” says Fuher.
Instead of using simple keylogging programs on the individual desktop which can be easily disabled, or incurring the expense of new servers and maintaining server software, Nulty-Beals implemented iPrevision’s Panoptech™ “single-box” solution.
The “single-box” is a network appliance about the size of a cable TV or satellite signal receiver. As information or packets of data pass in and out of the agency, the Panoptech box scans and caches information, URLs, and more in order to not only analyze and monitor usage but also to minimize any congestion. From a technical standpoint, iPrevision manages all of the content and software updates from their end, because “we don’t want to create more IT work for an employee,” says Fuher.
Fuher says that once the inconspicuous-looking appliance is delivered to an agency, installation is not much more than taking it out of the box and plugging it into the network. “With Nulty Insurance,” notes Kellner, “within 10 minutes they were up and running and seeing usage data.”
Real-time data
Panoptech offers on-demand, real-time reporting on Internet, IM, and Web usage. Since the system is connected to the network, those who administer, monitor or review the data can do so from their office, from home or another remote location, which makes monitoring of multiple or branch offices much easier.
Nulty-Beals says, “We just use it for Internet monitoring right now—just to see how the Internet is being used in our office. We’re not using it for filtering.”
Internet monitoring reports show user name, their IP address, the computer name, date and time stamp, and a URL with clickable link. “We’ve had stories of people coming in after hours, even cleaning staff using the network, so having detailed information is key,” says Kellner.
“In one instance,” he recalls, “an agency had been running the system for only a week and when they went to do employee training, their reports showed that some employees had been downloading inappropriate material. After dealing with that eye-opener, they now say their reports are ‘kind of boring.’”
Panoptech makes it easy for managers or owners to set filters for Web sites or types of sites. For example, with a single click on the “porn” check box, Panoptech will automatically filter out over 1.3 million active pornography sites thereby denying access to anyone trying to visit one of those sites. “We have ‘bots’ that continually look for sites, putting them into categories ranging from shopping and sports to entertainment and porn,” says Fuher. “But, we also leave it customizable so you could filter out all shopping but still allow eBay—so basically, we’re letting you create your own white- and blacklists.”
Panoptech also monitors IM usage, tracking usernames and logging all conversations to and from “buddies.” Besides being able to monitor IM usage on most of the common IM formats/protocols like Yahoo, MSN, AOL and even IRC, The Panoptech solution also gives agencies a good way to meet reten-tion policies for IM communication. As with all of the other monitoring and filtering capabilities for Internet and Webmail usage, specific employees or groups of employees can be blocked from any and all IM usage.
With Internet browsers, P2P programs and IM clients all residing on the individual’s computer, Webmail is a little trickier because it resides on another server, and access to an e-mail account still requires a username and password. Panoptech, however, is able to take virtual “snapshots” of the employee’s activity and reconstruct messages that could potentially put the agency at risk.
“In the past, Internet monitoring was handled by the IT staff—usually reactively after something happened,” says Fuher. “For small agencies without an IT person, it’s difficult to implement an enforceable usage policy, so we try to provide a scalable, manageable—and yet affordable—service that shows an almost immediate return on investment.”
“Whether you have 10 offices or one office, agency owners or managers now have an eye into those offices to see how their employees are using the Internet,” says Kellner. “It really hits home for them when they can see the reports and the usage, and that data can help them evolve their policies and plans. So if they run a report showing the top domains visited by their employees and none of their carrier or customer sites show up on the list, it becomes easier to address.”
“For the most part, and for whatever reason, a lot of these Internet applications have been off of our radar,” says Nulty-Beals, “but the more I learn about how they can be used, the more I’m thinking they shouldn’t be off of our radar.” *
For more information:
iPrevision
Web site: www.iprevision.net
The author
John Chivvis is a Texas-based writer who specializes in topics of technology implementation. His work has appeared in a number of national and regional publications. |
|
Click on image for enlargement |
 |
| |
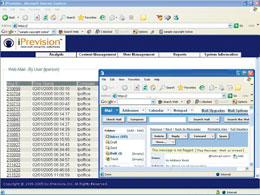
| Panoptech monitors Webmail accounts accessed from within the network. Moreover, activity is recorded and stored, giving the organization a complete, up-to-the-minute view of suspicious or risky behavior. |
| |
 |
| |
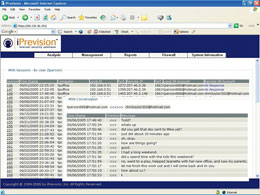
| Instant Messaging (IM) monitoring provides the organization with the means to implement, monitor, and administer a thorough IM retention policy. In addition, it helps protect internal data from unauthorized transmission. |
| |
 |
| |
| Panoptech monitors the Web traffic flowing through the network, recording Internet usage by user name, internal IP address, computer name, date and time of the session, and the URL or Web address visited. |
| |
 |
| |
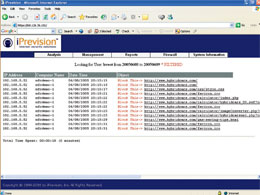
| To evaluate how much time is spent by a user on any particular site, the reports can be filtered to include the specific date and time a user accessed any one specific site. |
|


