
THE “WHEN” NOT “IF”
WORLD OF CYBER RISK
The statistics are startling; the role of cyber risk consultant is now critical
By Carolyn Smith, TRA, ASA
Many small business owners believe that they are too small to be hacked. In truth, no one is immune from a cyber incident … and the statistics are startling:
The average cost of a data breach involving ransomware, according to IBM’s 2021 Cost of a Data Breach Report, is $4.62 million (USD).
- A 2021 survey on ransomware by Lookout/Pulse reports that 57% of security leaders believe they will experience a ransomware attack within the next year.
- The average impact from ransomware attacks cost one month of recovery time, negatively affected a business’s ability to operate, and caused 86% to lose business and/or revenue, according to Sophos’ The State of Ransomware 2022 report.
The frequency of ransomware and other cyberattacks creates an increasingly
dangerous cyber landscape for small and mid-sized businesses.
Providing value as a trusted advisor
This is where you come in as a trusted advisor, a risk consultant who educates clients on cyber risk management.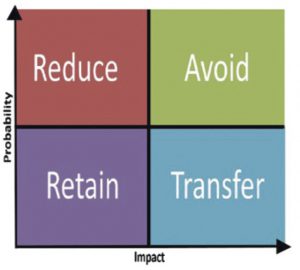
Consider the risk decision matrix (shown here), then ask yourself:
- How can my clients proactively prepare before an attack even happens? (avoid)
- How can I help my clients reduce their cyber risk?
When a business fails to reduce its cyber risk, it jeopardizes its business continuity and reputation in the event of a breach. Very few small and mid-sized businesses have the necessary resources to recover from a cyberattack.
However, like any risk, the threat of a cyberattack can be managed for any size or type of organization using the five-step risk management process: 1) Identify, 2) Analyze, 3) Evaluate, 4) Implement, 5) Monitor.
NIST framework
To improve critical cybersecurity infrastructure, the National Association of Insurance Commissioners (NAIC) recommends implementing the National Institute of Standards and Technology (NIST) framework (see page 75) to help manage cyber risks.
It is broken down into five steps: Identify, Protect, Detect, Respond, and Monitor. And it has some basic practices you can help your clients take immediately to protect their data and information.
Some risk consultants who specialize in cyber risk see the need to take these two processes further.
The Mid-State Group (themidstategroup.com) in Lynchburg, Virginia, has embraced the NIST framework and combined it with the risk management process to ensure that its clients comply with stringent data protection and privacy regulations.
“Since the pandemic began, cyberattacks have increased over 600% with 43% targeting vulnerable small businesses. Sixty percent of these small businesses will go out of business within six months of an attack. It’s not a matter of if you get attacked but when, and can your business recover? The only proven method to protect, detect, respond, and recover from a cyber incident is to follow an industry best practice such as NIST Cybersecurity Frame-work,” said John Basten, president and chief growth officer of The Mid-State Group.
To use this combination framework with your clients, schedule a ransomware readiness consultation. Then use active listening during steps one through three to uncover what keeps your client up at night.
Step 1: Identify. Identify an organization’s greatest points of vulnerability, exposure, and most valuable assets. Include business environment, governance, and preparedness against ransomware.
During this step, you should identify where your clients house and store customer data and discover any related risks.
Step 2: Assess and Protect. Conduct a cyber risk assessment that can include identifying gaps in their existing policies and reviewing their potential threat landscape. Help the client assess the business’s cyber aware-ness and training, employee policies and guidelines; the strength of its security infrastructure and data security; and protective technology, including end-point protection for desktops, laptops, mobile devices, and servers.
This step includes assessing insider threats such as employee work-from-home (WFH) risks, Bring Your Own Device (BYOD) risks (employees bringing their own devices to work), Mobile Device Management (MDM) policies, and Shadow IT risks (employees downloading any application or cloud service to make their jobs easier that inadvertently can lead to sensitive data exposure, e.g., Dropbox, GoogleDocs, etc.).
In addition, you should assess any client businesses that offer free Wi-Fi to customers, such as gyms, hotel business centers, coffee shops, and fast-food shops. This step also includes determining if the business’s third-party vendors and suppliers, such as accountants and attorneys, are protecting the privacy and security of your client’s data.
Step 3: Evaluate and Detect. Develop strategies and a cyber risk prevention and treatment plan that includes regulatory/compliance guidance for the client. Uncover any anomalies and malicious cyber events. Help the client find an effective detection process. Evaluate the client’s resources and budget needed to implement a cyber resilience and recovery plan.
This step is where you determine your client’s risk tolerance and use the risk decision matrix with them. Remember that even using this cyber-security framework, it is impossible for any business to be completely protected from cyber threats. It is your role as the trusted advisor to assist the business owner in focusing on areas that would have the greatest impact on business continuity.
Step 4: Implement and Respond. This should include a practical cybersecurity playbook that will work in the event of a cyber attack. It should also include plans for cyber incident response, communication, mitigation, and improvements needed in the business’s security posture.
In this step, in addition to ensuring the business has a cybersecurity incident response plan, you would help your clients mitigate their cyber risk through comprehensive cyber insurance. According to the Insurance Information Institute (III), cyber insurance “lowers the cost to a business … by covering damages that general liability insurance may not, including legal fees, repairing digital infrastructure, resorting clients’ personal information, and recovering proprietary data.”
Step 5: Monitor and Recover. Communicate with the client on a monthly basis to ensure that the organization’s cybersecurity is continuously improving. Ensure that the recovery plan is in place and ready to be implemented in case of a cyber attack.
During this step, you must help your clients monitor their cybersecurity plan and its effectiveness on an ongoing basis. The rate of being victimized by a cyber attack is growing at an alarming rate, and new threats emerge continuously.
Cyber liability coverage helps mitigate cyber risks
The Sophos Report shows that, while cyber insurance helps organizations recover from a ransomware attack, far too many small and medium-sized business owners fail to purchase appropriate levels of coverage or, worse, fail to reduce their ransomware risk and exposure.
At the same time, Sophos found that 94% of organizations with cyber insurance said that “their experience of getting it has changed over the last 12 months, with higher demands for cybersecurity measures, more complex or expensive policies, and fewer organizations offering insurance protection.”
Fortunately, in addition to focusing on improving your clients’ cyber resilience, you as a trusted advisor are well-positioned to partner with insurers to help mitigate the risks posed by a potential cyber attack. Why?
The frequency of ransomware and other cybe attacks creates an increasingly dangerous cyber landscape for small and mid-sized businesses. They desperately need cyber insurance, yet it is growing increasingly difficult to secure. Insurers are reluctant to take on more cyber risk, while added coverage limitations and exclusions leave small and mid-sized businesses exposed or paying significantly higher premiums.
The NAIC’s Report on the Cyber-security Insurance Market states, “Changes regarding risk factors are occurring in the underwriting process. Underwriters are starting to use tools to evaluate prospective insureds’ computer networks to decide whether they will write the cyber business … . [P]remiums grew substantially in 2020 as cyber threats, particularly those having to do with ransomware, continue to rise … . While businesses are aware that cyber risk is a looming issue, it is not uncommon for policy-holders to believe their current business insurance policy covers a cyber loss.”
Insurers are tightening the proverbial reins, asking more granular questions about a business’s cyber resilience, and diving deeply into small and mid-sized businesses’ claims and loss history while simultaneously including capacities, exclusions, and segmented coverages—all at a higher premium. According to the NAIC, insurers are exiting accounts that do not have controls in place. They expect superior data on an applicant’s risk posture before binding and want you to detail your assessment of the business’s risk exposure and tolerance.
“Implementing carrier-required security controls is not only in the insurer’s best interest. It also benefits the policyholder. It can help soften premium increases, improve coverage, and can greatly reduce the odds of a successful attack. Anyone who has ever been involved in a cyber event will tell you it was a painful experience. The cost associated with such an attack can easily far surpass the cost to have implemented the preventative measures in the first place,” said Hank Stickley, senior vice president, and Cynthia Zimmerman, executive vice president, of Socius Insurance Services (sociusinsurance.com).
When you collaborate with your clients as a cyber risk consultant by combining the risk management and NIST processes, you are well-poised to reduce cyber risk, help businesses remain solvent and resilient, and provide them with full coverage that offers robust protection. The cyber risk consultant … a critical role in the “when, not if world” of cybersecurity.
The author
Carolyn Smith is the director of marketing and innovation for Beyond Insurance and a performance coach for the Quest for Success and Reach Your Peak six-month coaching, mentoring, and performance-enhancement programs. Beyond Insurance is a premier coaching and training organization for insurance agents, brokers, and carriers who desire a consultative, diagnostic customer engagement process.




